RemoteIoT VPC Network has become a critical component for organizations aiming to secure and manage their IoT infrastructure in the cloud. As more devices become connected, the need for a robust and scalable virtual private cloud (VPC) network has never been more important. In this article, we will delve into the intricacies of RemoteIoT VPC networks, exploring their architecture, benefits, challenges, and best practices.
With the rapid expansion of IoT deployments worldwide, businesses are increasingly relying on cloud-based solutions to streamline operations and enhance connectivity. A well-structured RemoteIoT VPC network plays a pivotal role in ensuring secure communication between devices, applications, and users. This article will provide you with an in-depth understanding of how RemoteIoT VPC networks function and why they are essential for modern IoT ecosystems.
Whether you're an IT professional, a network administrator, or simply someone interested in cloud computing and IoT integration, this guide will equip you with the knowledge needed to design, deploy, and optimize your RemoteIoT VPC network. Let’s dive in.
Read also:Baywatch 2 Release Date The Ultimate Guide To The Sequel
Table of Contents
- What is RemoteIoT VPC Network?
- Benefits of Using RemoteIoT VPC Network
- Key Components of RemoteIoT VPC Network
- Architecture of RemoteIoT VPC Network
- How to Set Up RemoteIoT VPC Network
- Security Considerations for RemoteIoT VPC Network
- Challenges in Implementing RemoteIoT VPC Network
- Best Practices for RemoteIoT VPC Network
- Use Cases of RemoteIoT VPC Network
- Future of RemoteIoT VPC Network
What is RemoteIoT VPC Network?
A RemoteIoT VPC Network refers to a virtual private cloud environment specifically designed for managing Internet of Things (IoT) devices and applications. This network allows organizations to create an isolated section within a public cloud, ensuring secure communication between IoT devices, servers, and end-users.
The primary purpose of a RemoteIoT VPC network is to provide a secure and scalable infrastructure for IoT deployments. By leveraging VPC capabilities, organizations can control access, monitor traffic, and implement advanced security measures to protect sensitive data.
Definition and Importance
RemoteIoT VPC networks are crucial for maintaining privacy and security in IoT ecosystems. They enable businesses to:
- Isolate IoT workloads from other cloud resources.
- Control inbound and outbound traffic using security groups and access control lists (ACLs).
- Scale resources dynamically to accommodate growing IoT device fleets.
Benefits of Using RemoteIoT VPC Network
Implementing a RemoteIoT VPC network offers numerous advantages that contribute to the efficiency and security of IoT operations. Below are some of the key benefits:
Enhanced Security
RemoteIoT VPC networks provide robust security features, including:
- Encrypted communication between devices and servers.
- Network segmentation to isolate IoT traffic.
- Advanced threat detection and mitigation capabilities.
Scalability and Flexibility
With a RemoteIoT VPC network, organizations can easily scale their IoT infrastructure to meet changing demands. This flexibility ensures that businesses can accommodate growth without compromising performance or security.
Read also:Otogibanashio Onigokko A Comprehensive Guide To The Iconic Japanese Folklore Game
Cost Efficiency
By leveraging cloud-based solutions, companies can reduce capital expenditures associated with traditional on-premises infrastructure. RemoteIoT VPC networks allow for pay-as-you-go pricing models, making them cost-effective for organizations of all sizes.
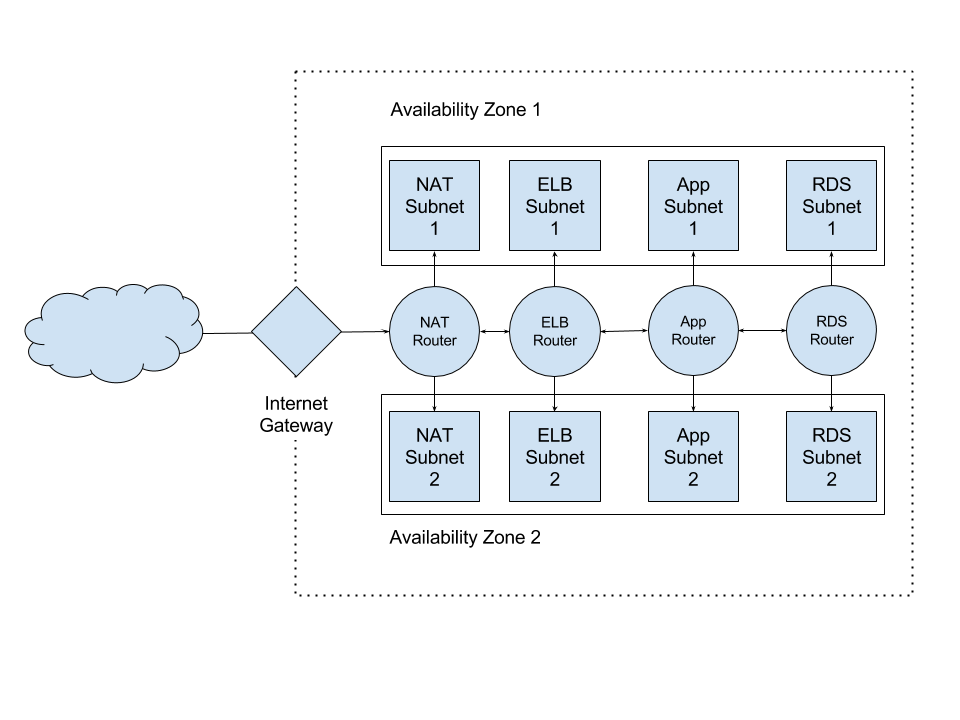
Key Components of RemoteIoT VPC Network
A RemoteIoT VPC network consists of several essential components that work together to ensure seamless operation and security. These include:
Subnets
Subnets divide the VPC into smaller segments, allowing for better traffic management and resource allocation. Public subnets enable direct internet access, while private subnets remain isolated from external networks.
Security Groups
Security groups act as virtual firewalls, controlling inbound and outbound traffic at the instance level. They define rules for allowing or denying specific types of traffic, enhancing the overall security of the network.
Access Control Lists (ACLs)
ACLs provide an additional layer of security by controlling traffic at the subnet level. They can be used to whitelist or blacklist specific IP addresses, ensuring that only authorized devices and users can access the network.
Architecture of RemoteIoT VPC Network
The architecture of a RemoteIoT VPC network is designed to ensure high availability, scalability, and security. Key architectural elements include:
Multi-tier Architecture
A multi-tier architecture separates the network into distinct layers, such as web, application, and database tiers. This separation enhances security and improves performance by isolating critical components.
Load Balancers
Load balancers distribute incoming traffic across multiple instances, ensuring optimal resource utilization and minimizing downtime. They also provide failover capabilities, enhancing the reliability of the network.
Internet Gateways
Internet gateways enable communication between the VPC and the public internet. They allow devices within the VPC to access external resources while maintaining a secure connection.
How to Set Up RemoteIoT VPC Network
Setting up a RemoteIoT VPC network involves several steps, including:
Step 1: Define Network Requirements
Before creating a VPC, it’s essential to determine the specific needs of your IoT deployment. Consider factors such as the number of devices, expected traffic volume, and security requirements.
Step 2: Create Subnets
Divide the VPC into public and private subnets to ensure proper traffic management and resource allocation. Assign IP address ranges to each subnet based on your network requirements.
Step 3: Configure Security Settings
Set up security groups and ACLs to control access to the network. Define rules for allowing or denying specific types of traffic, ensuring that only authorized devices and users can connect.
Security Considerations for RemoteIoT VPC Network
Securing a RemoteIoT VPC network requires a multi-faceted approach that addresses potential vulnerabilities at every level. Key considerations include:
Data Encryption
Encrypting data both in transit and at rest is critical for protecting sensitive information. Use industry-standard encryption protocols, such as TLS and AES, to ensure data confidentiality.
Identity and Access Management (IAM)
Implement strict IAM policies to control user access to the network. Assign roles and permissions based on the principle of least privilege, ensuring that users only have access to the resources they need.
Intrusion Detection and Prevention
Deploy intrusion detection and prevention systems (IDPS) to monitor network traffic for suspicious activity. These systems can help identify and mitigate potential threats before they cause harm.
Challenges in Implementing RemoteIoT VPC Network
While RemoteIoT VPC networks offer numerous benefits, there are also challenges to consider when implementing them. Common challenges include:
Complexity of Configuration
Setting up and configuring a VPC network can be complex, especially for organizations with limited cloud expertise. Proper planning and documentation are essential to ensure successful deployment.
Resource Management
Managing resources within a VPC network requires careful planning and monitoring. Organizations must ensure that they have sufficient capacity to accommodate growing IoT fleets while avoiding unnecessary costs.
Security Threats
IoT devices are often targeted by cybercriminals, making security a top priority for VPC networks. Organizations must stay vigilant and continuously update their security measures to protect against evolving threats.
Best Practices for RemoteIoT VPC Network
To maximize the benefits of a RemoteIoT VPC network, organizations should adhere to the following best practices:
Regular Audits and Assessments
Conduct regular security audits and assessments to identify vulnerabilities and ensure compliance with industry standards. This proactive approach helps mitigate risks and enhances overall network security.
Continuous Monitoring
Implement continuous monitoring tools to track network activity and detect anomalies in real-time. This enables organizations to respond quickly to potential threats and minimize downtime.
Employee Training
Provide ongoing training for employees on cloud security best practices and IoT management. Educating staff on the importance of security helps foster a culture of responsibility and accountability.
Use Cases of RemoteIoT VPC Network
RemoteIoT VPC networks are applicable in various industries and use cases, including:
Smart Cities
Smart city initiatives rely on IoT devices to monitor and manage infrastructure, such as traffic lights, energy grids, and waste management systems. A RemoteIoT VPC network ensures secure communication between these devices and centralized control systems.
Healthcare
In healthcare, IoT devices are used for remote patient monitoring, telemedicine, and medical device management. A RemoteIoT VPC network provides the security and reliability needed to protect sensitive patient data.
Manufacturing
Manufacturing facilities use IoT sensors to monitor equipment performance and optimize production processes. A RemoteIoT VPC network enables real-time data collection and analysis, improving efficiency and reducing downtime.
Future of RemoteIoT VPC Network
The future of RemoteIoT VPC networks looks promising, with advancements in technology driving innovation and adoption. Key trends to watch include:
Edge Computing Integration
Edge computing will play a significant role in the evolution of RemoteIoT VPC networks, enabling faster data processing and reduced latency. By bringing computation closer to the source of data, edge computing enhances the performance and reliability of IoT deployments.
Artificial Intelligence and Machine Learning
AI and ML technologies will further enhance the capabilities of RemoteIoT VPC networks by providing predictive analytics and automated decision-making. These technologies will help organizations optimize their IoT infrastructure and improve overall efficiency.
Quantum Computing
As quantum computing becomes more mainstream, it will revolutionize the way RemoteIoT VPC networks are designed and operated. Quantum encryption and advanced algorithms will provide unprecedented levels of security and performance.
Conclusion
RemoteIoT VPC networks are essential for securing and managing IoT deployments in the cloud. By understanding their architecture, benefits, and challenges, organizations can harness the full potential of these networks to drive innovation and growth.
We encourage you to implement the best practices outlined in this article and explore the various use cases of RemoteIoT VPC networks. Share your thoughts and experiences in the comments below, and don’t forget to check out our other articles for more insights into cloud computing and IoT integration.