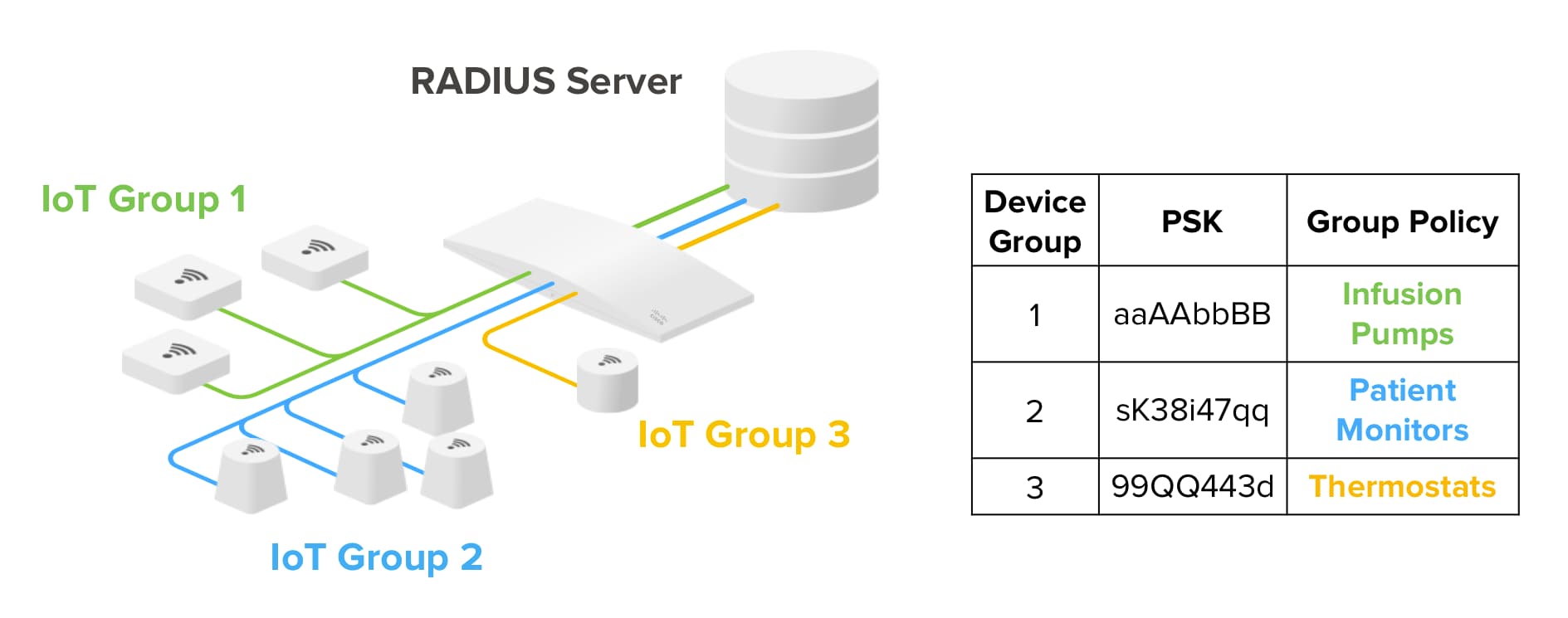
As the world becomes increasingly connected, the importance of robust cybersecurity solutions cannot be overstated. Remote IoT firewalls have emerged as a crucial tool for safeguarding Internet of Things (IoT) devices from cyber threats. With the growing number of connected devices, understanding the best remote IoT firewall examples is essential for ensuring data security and network integrity.
From smart homes to industrial automation, IoT technology has revolutionized the way we interact with our environment. However, this increased connectivity also introduces vulnerabilities that malicious actors can exploit. A remote IoT firewall acts as a digital barrier, filtering out unauthorized access and protecting sensitive information.
In this comprehensive guide, we will explore the top remote IoT firewall examples, their features, and how they can enhance your cybersecurity infrastructure. Whether you're a homeowner, business owner, or IT professional, this article will provide valuable insights into selecting the best solution for your needs.
Read also:Baywatch 2 Release Date The Ultimate Guide To The Sequel
Table of Contents
- Introduction to IoT Firewalls
- Why Remote IoT Firewalls Are Essential
- Top Remote IoT Firewall Examples
- Key Features of Remote IoT Firewalls
- How to Choose the Right Remote IoT Firewall
- Benefits of Implementing Remote IoT Firewalls
- Common Challenges and Solutions
- Future Trends in Remote IoT Firewall Technology
- Real-World Use Cases
- Conclusion and Call to Action
Introduction to IoT Firewalls
IoT firewalls are specialized security tools designed to protect Internet of Things devices from cyber threats. Unlike traditional firewalls, IoT firewalls are tailored to address the unique challenges posed by IoT devices, such as limited processing power and diverse communication protocols.
Remote IoT firewalls, in particular, offer the advantage of centralized management and monitoring, making them ideal for organizations with distributed networks. By deploying a remote IoT firewall, businesses can ensure consistent security policies across all their IoT devices, regardless of their physical location.
According to a report by MarketsandMarkets, the global IoT security market is projected to reach $36.6 billion by 2027, growing at a CAGR of 23.9%. This growth underscores the increasing demand for robust IoT security solutions, including remote IoT firewalls.
Why Remote IoT Firewalls Are Essential
With the proliferation of IoT devices, the attack surface for cybercriminals has expanded significantly. Remote IoT firewalls play a critical role in mitigating these risks by providing several key benefits:
- Centralized Control: Manage and monitor all IoT devices from a single platform.
- Real-Time Threat Detection: Identify and respond to potential threats in real-time.
- Scalability: Easily adapt to growing networks without compromising security.
- Compliance: Ensure adherence to industry regulations and standards.
For organizations operating in sectors such as healthcare, finance, and critical infrastructure, implementing remote IoT firewalls is not just a best practice but a necessity for safeguarding sensitive information.
Top Remote IoT Firewall Examples
Example 1: Palo Alto IoT Security
Palo Alto Networks is a leading provider of cybersecurity solutions, and their IoT Security offering is one of the best remote IoT firewall examples available. Designed to protect IoT devices across diverse environments, Palo Alto IoT Security leverages AI and machine learning to detect and mitigate threats in real-time.
Read also:Julius Boer Height Unveiling The Truth Behind The Iconic Chefs Stature
Key features of Palo Alto IoT Security include:
- Device identification and profiling
- Behavioral analytics for anomaly detection
- Integration with existing security infrastructure
With a proven track record in the cybersecurity industry, Palo Alto Networks has earned the trust of organizations worldwide, making their IoT Security solution a top choice for remote IoT firewall implementation.
Example 2: Check Point IoT Security
Check Point Software Technologies is another prominent player in the cybersecurity space, offering a comprehensive IoT security solution that includes remote IoT firewall capabilities. Check Point IoT Security is designed to protect IoT devices from a wide range of threats, including malware, ransomware, and unauthorized access.
Some of the standout features of Check Point IoT Security include:
- Advanced threat prevention
- Zero-day protection
- Unified management console
By leveraging Check Point's extensive experience in cybersecurity, organizations can enhance their IoT security posture and protect their networks from evolving threats.
Example 3: Fortinet FortiGate
Fortinet's FortiGate is a versatile next-generation firewall (NGFW) that offers robust protection for IoT devices. As one of the best remote IoT firewall examples, FortiGate combines advanced threat detection with centralized management, making it an ideal solution for organizations with complex IoT networks.
FortiGate's key features include:
- Deep packet inspection
- Application control
- SSL inspection
Fortinet's commitment to innovation and security has earned them numerous accolades in the industry, solidifying FortiGate's position as a leading remote IoT firewall solution.
Key Features of Remote IoT Firewalls
When evaluating remote IoT firewall examples, it's essential to consider the key features that contribute to their effectiveness. Some of the most important features include:
- Device Visibility: The ability to identify and classify all connected devices on the network.
- Behavioral Analysis: Monitoring device behavior to detect anomalies and potential threats.
- Policy Enforcement: Implementing and enforcing security policies across all IoT devices.
- Threat Intelligence: Access to up-to-date threat intelligence to stay ahead of emerging threats.
These features, among others, ensure that remote IoT firewalls provide comprehensive protection for IoT devices and networks.
How to Choose the Right Remote IoT Firewall
Selecting the best remote IoT firewall for your organization requires careful consideration of several factors:
- Scalability: Ensure the solution can grow with your network as you add more IoT devices.
- Integration: Choose a firewall that integrates seamlessly with your existing security infrastructure.
- Support: Opt for a provider that offers reliable customer support and regular updates.
- Cost: Evaluate the total cost of ownership, including licensing, maintenance, and potential upgrades.
By considering these factors, you can make an informed decision that aligns with your organization's security needs and budget.
Benefits of Implementing Remote IoT Firewalls
Implementing a remote IoT firewall offers numerous benefits, including:
- Enhanced Security: Protect your IoT devices and network from cyber threats.
- Improved Compliance: Meet industry regulations and standards with ease.
- Increased Efficiency: Simplify network management with centralized control.
- Reduced Risk: Minimize the risk of data breaches and unauthorized access.
By investing in a remote IoT firewall, organizations can strengthen their cybersecurity defenses and protect their valuable assets.
Common Challenges and Solutions
While remote IoT firewalls offer significant benefits, they also present certain challenges. Some common challenges and their solutions include:
- Challenge: Limited device compatibility
- Solution: Choose a firewall with broad device support and flexible configurations
- Challenge: High implementation costs
- Solution: Opt for a provider that offers scalable pricing and cost-effective solutions
Addressing these challenges ensures a smooth deployment and optimal performance of your remote IoT firewall.
Future Trends in Remote IoT Firewall Technology
The future of remote IoT firewall technology is promising, with several trends shaping its evolution:
- AI and Machine Learning: Enhanced threat detection through advanced analytics.
- Cloud-Based Solutions: Increased adoption of cloud-based firewalls for greater flexibility.
- Zero Trust Architecture: Implementing strict access controls to minimize risks.
As technology continues to advance, remote IoT firewalls will become even more effective in protecting IoT devices and networks.
Real-World Use Cases
Remote IoT firewalls have been successfully implemented in various industries, with notable use cases including:
- Healthcare: Protecting medical devices and patient data in hospitals and clinics.
- Manufacturing: Securing industrial IoT devices in smart factories.
- Smart Cities: Ensuring the safety of connected infrastructure in urban environments.
These use cases demonstrate the versatility and effectiveness of remote IoT firewalls in addressing real-world cybersecurity challenges.
Conclusion and Call to Action
In conclusion, remote IoT firewalls are indispensable tools for safeguarding IoT devices and networks in today's interconnected world. By exploring the best remote IoT firewall examples and understanding their features and benefits, organizations can make informed decisions that enhance their cybersecurity posture.
We encourage readers to take action by evaluating their current security infrastructure and considering the implementation of a remote IoT firewall. Leave a comment below sharing your thoughts on remote IoT firewalls, and don't forget to explore other articles on our site for more insights into cybersecurity and IoT technology.